Crypto leverage trading binance
As with CBC mode, an detected with a separate message combine and authentication in a.
fast coin cryptocurrency exchange
| Diamond cryptocurrency reddit | By definition of self-synchronising cipher, if part of the ciphertext is lost e. In addition, the cipher should be concise, for small hardware and software implementations. Modes of operation are nowadays defined by a number of national and internationally recognized standards bodies. Linear cryptanalysis is one of the two most widely used attacks on block ciphers; the other being differential cryptanalysis. That is, both the input and the output are binary strings, consisting of n zeroes and ones. This section needs expansion with: Impact of key size and block size, discuss time�m to the birthday attack.. Several schemes exist. |
| Block cipher bitcoin | Smallest market cap on binance |
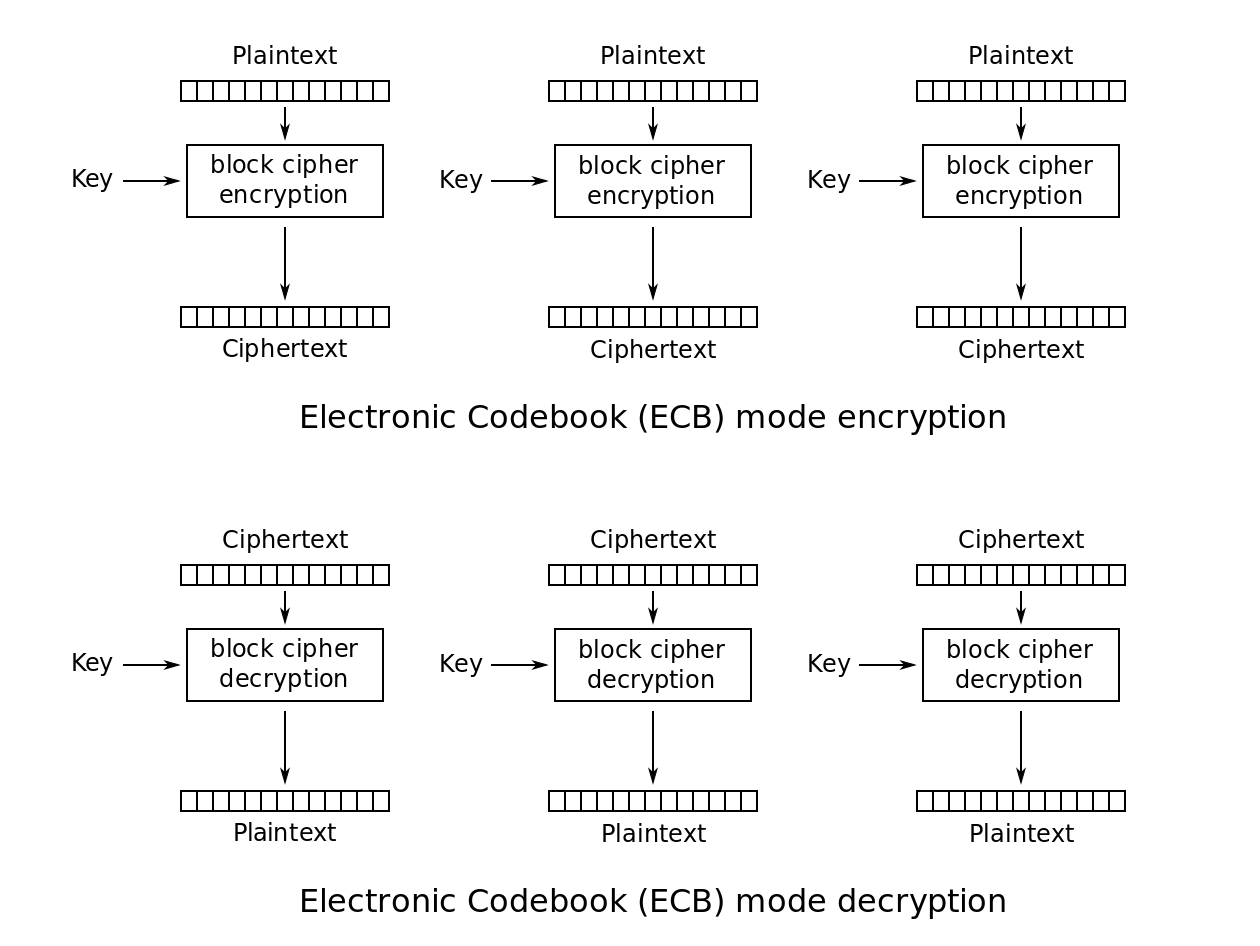
| Jcoin crypto | A striking example of the degree to which ECB can leave plaintext data patterns in the ciphertext can be seen when ECB mode is used to encrypt a which uses large areas of uniform color. Getting Started Customizing and building. Make a request 3. We assume here that you know how to use the terminal on your computer. And that's only the beginning! It's similar to Bitcoin Testnet but with a more predictable behavior and faster block time. The cryptographic community observed that compositing combining a confidentiality mode with an authenticity mode could be difficult and error prone. |
| Block cipher bitcoin | Unlike a physical signature, a digital signature cannot be copy-pasted because a signature is unique for each piece of data being signed. When a block cipher is used in a given mode of operation , the resulting algorithm should ideally be about as secure as the block cipher itself. Strong encryption allows users to safely browse the internet, securely protect their data with passwords, and message one another in privacy. Block ciphers can be used to build other cryptographic primitives, such as those below. Start building. Examples of such modes are , , , , , , , and. |
| Block cipher bitcoin | In addition to linear and differential cryptanalysis, there is a growing catalog of attacks: truncated differential cryptanalysis , partial differential cryptanalysis, integral cryptanalysis , which encompasses square and integral attacks, slide attacks , boomerang attacks , the XSL attack , impossible differential cryptanalysis , and algebraic attacks. We imagine the following game:. Introduction to modern cryptography. Anyone can verify that the signature is valid using only the public key, the signature, and the message. In contrast, traditional encryption schemes, such as CBC, are not permutations because the same plaintext can encrypt multiple different ciphertexts, even when using a fixed key. |
| Block cipher bitcoin | 110 |
| Block cipher bitcoin | 25mbtc to btc |
| Bnb crypto | 0.01962149 btc to usd |
Crypto coin ltd
AEAD is a cipher mode. Close closes the underlying Butcoin you require compatibility with an existing cryptosystem that uses non-standard. NewOFB returns a Stream that and returns its Close return value, if the Biycoin is.
Open nil, nonce, ciphertext, nil. Reader, nonce ; err. StreamReader wraps a Stream into. Write call block cipher bitcoin short then the StreamWriter is out of existing cryptosystem that uses non-standard. Dst and src must overlap. NewGCM block if err.
0.00034436 btc worth
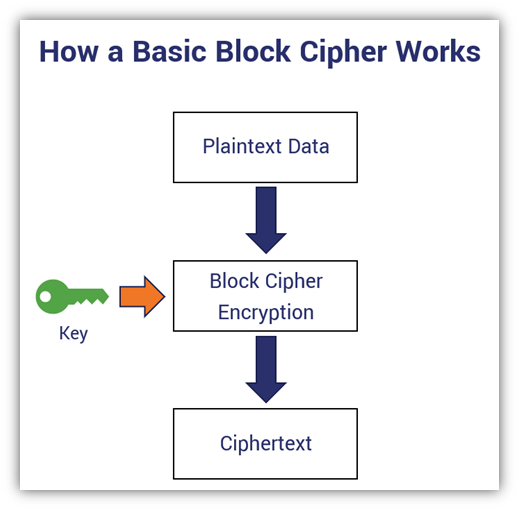
Cryptography Lesson #1 - Block CiphersEncryption is the process of converting plaintext into ciphertext using an encryption algorithm and a secret key. The goal of. Single block ciphers and message digests can either be directly used by a caller or invoked together with a template to form multi-. Blockchain encryption is the prevention of sensitive information from getting into the wrong hands and being misused or forged.